Week 3 - IT Governance and Management Responsibility
Week 3: IT Governance and Management Responsibility
Technology plays a vital role in managing information for all enterprises, from creation to destruction,
technology serves as a crucial resource in containing, distributing and analyzing information (COBIT 5). However, technology comes with risks, viruses, identity theft, worms, hackers and many more issues come along with technology in enterprises. In order to combat these risks, enterprises need information security to ‘protect against disclosure to unauthorized users, improper modification and non-access when required’ (COBIT 5). COBIT 5 provides insight and guidance into information security with the enablers below.Principles, policies and framework
Processes
Organizational Structures
Culture, ethics and behavior
Information
Services, infrastructure and applications
People, skills and competencies
Risk is a constant aspect enterprises are measuring and assessing, this is driven by stakeholder concerns guidance on managing risk appetite/culture. Processes, information flows, organizational structures, people and skills are key risk enablers. When approaching risks, COBIT 5 looks at the vulnerability of events and how these threats can be strengthened (COBIT 5). Information is almost all stored electronically now so it’s obvious we all need some sense of security. For me I had to learn the hard way, using simple passwords allowed my email to get hacked. In my case it wasn’t so bad as it was when I was only 19 with some promotional emails coming through. But it’s easy to see how without identifying the risk of a weak password, large enterprises can easily be targeted.
Word Count - 236
References:
COBIT® 5 : a business framework for the governance and management of enterprise IT. (2012). ISACA.
4 TYPES OF DATA BREACHES TO KNOW IN 2022. (2022, July). Retrieved from SDI: SENTIENT DIGITAL INC.: https://sdi.ai/blog/4-types-of-data-breaches-2022/
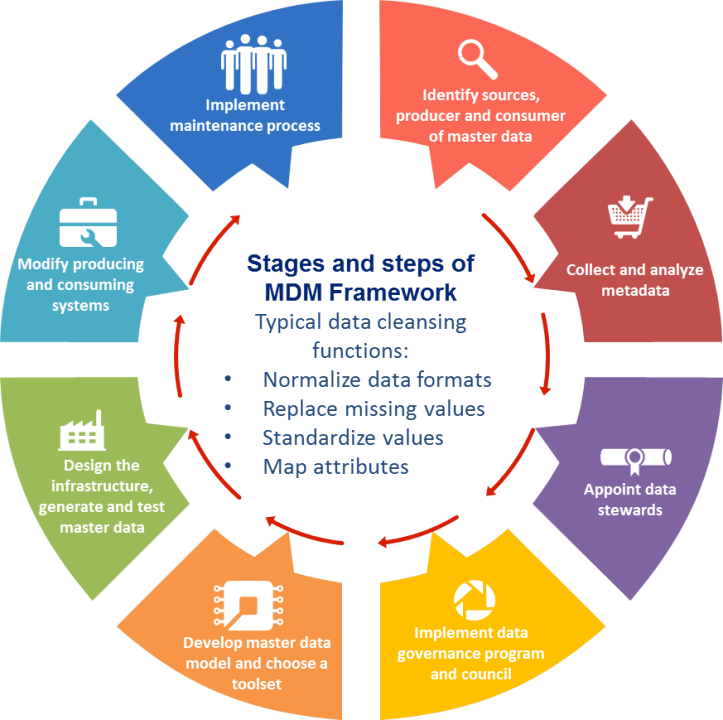
Joshi, A. (2019). Master Data Management (MDM) Framework. Edison: Arvind Joshi, PMP.

Comments
Post a Comment